New Updated 352-001 Exam Questions from PassLeader 352-001 PDF dumps! Welcome to download the newest PassLeader 352-001 VCE dumps: https://www.passleader.com/352-001.html (738 Q&As)
Keywords: 352-001 exam dumps, 352-001 exam questions, 352-001 VCE dumps, 352-001 PDF dumps, 352-001 practice tests, 352-001 study guide, 352-001 braindumps, CCDE Design Written Exam, v2.1
P.S. New CCDE 352-001 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpflFYOFdyS1ctQVc2X1cwT0d2R2dyZzBsb2hPaGw5V2Y5akx5QmxxYUdOOUU
NEW QUESTION 706
What are two base components of both a source-based remotely triggered black hole and a destination-based remotely triggered black hole filtering solution? (Choose two.)
A. NetFlow
B. static route withthe next hop pointing to the Null0 interface
C. infrastructure access list
D. triggered IBGP update setting next hop to a predetermined, unused IP address
E. uRPF
Answer: BD
NEW QUESTION 707
Which routing protocol requires minimal reconfiguration when establishing a MPLS Layer 3 VPN over DMVPN encrypted using GETVPN?
A. OSPF
B. RIP
C. IS-IS
D. BGP
Answer: D
NEW QUESTION 708
The campus consists of four main buildings with a single router at each location. A single Ethernet connection exists between each building. Which two EIGRP metrics should be made equal in the network redesign to ensure proper load sharing? (Choose two.)
A. Bandwidth
B. Load
C. Delay
D. Reliability
Answer: AC
NEW QUESTION 709
Which option is best suited to maintain Layer 3 separation in a multitenant data center design?
A. VXLAN
B. VRF
C. VDC
D. VLAN
Answer: B
NEW QUESTION 710
What is the key design principle for the core layer when using a classic hierarchical network model?
A. It is designed first, followed by thedistribution layer and then the access layer.
B. It controls access to resources for security.
C. It provides server access in asmall campus.
D. It should be configured with minimal complexity.
Answer: D
NEW QUESTION 711
Which statement about TAP and TUN devices, which are used in a Linux/KVM cloud deployment model, is true?
A. TUN is for handing IP packets, but TAP is for handing Ethernet frames.
B. TUN is for handing Ethernet frames, but TAP is for handing IP packets.
C. TUN is for tunneling IP packets, but TAP is for tapping IP packets.
D. TUN is for tunnelingEthernet frames, but TAP is for tapping Ethernet frames.
Answer: A
NEW QUESTION 712
Which two statements define some of the general characteristics of SDN? (Choose two.)
A. Southbound interfaces are interfaces used between the control plane and the date plane.
B. OpenFlow isconsidered one of the first Northbound APIs used by SDN controllers.
C. Northbound interfaces are open interfaces used between the control plane and the date plane.
D. The separation of the control plane from the data plane.
E. OVSDB is an application database management protocol.
Answer: AE
NEW QUESTION 713
A retail company has 250 branches connected to the core via MPLS Layer 3 VPN. The company is migrating from traditional telephony services to a VoIP solution. Which two primary concerns when implementing a VoIP solution are true? (Choose two.)
A. jitter
B. available bandwidth
C. call routing design
D. call routing design
E. MTU
F. SRST
Answer: AB
NEW QUESTION 714
A customer uses OSPF and BGP in their network. Which solution will continue forwarding packets during a temporary failure of a P node?
A. Deploy MPLS TE
B. Enable BGP Flowspec
C. Enable NSF/GR for OSPF
D. Deploy IS-IS an IGP instead of OSPF
Answer: A
NEW QUESTION 715
Which three factors effects the convergence times in an OSPF network? (Choose three.)
A. OSPF SPF throttling timers
B. OSPF pacing timers
C. OSPF LSA throttling
D. LSA refresh interval
E. DR/BDR election
F. OSPF LSA lifetime
Answer: ABC
NEW QUESTION 716
Video traffic is being distributed across a large WAN network. The video source originates from different parts of the multicast domain at different times. Which multicast technology provides optimal path selection between the receiver and the source for this multicast traffic?
A. Source Specific Multicast
B. PIM sparse mode
C. Bidirectional PIM
D. Any Source Multicast
Answer: A
NEW QUESTION 717
What are three common objectives for customers using multiple cloud providers? (Choose three.)
A. high availability
B. bandwidth
C. security
D. analytics
E. feature disparity
F. regional provider access
Answer: ABC
NEW QUESTION 718
For which two reasons would you deploy an IDS sensor in promiscuous mode when designing a security solution? (Choose two.)
A. The solution stops malicious traffic from reaching its intended target.
B. The solution allows denying packets inline.
C. The solution is resistant to sensor failure.
D. The solution allows for stream normalization.
E. The solution allows for signature-based pattern matching.
Answer: CE
NEW QUESTION 719
Today most of the enterprises are selecting container technologies that require integration with their existing data centers and infrastructure solutions. With which three factors do enterprises most commonly struggle to enable their current IT operations staff with? (Choose three.)
A. compliance
B. data security
C. performance and availability
D. cost avoidance
E. virtualization
F. data analytics
G. scalability
Answer: BCG
NEW QUESTION 720
Which two pain points are the most common for container technology adoption? (Choose two.)
A. container deployment
B. security
C. skilled staff
D. cost
E. compliance
F. performance
Answer: BC
NEW QUESTION 721
An enterprise company is attaching to a new Gigabit Ethernet-based link from the local service provider. This connection must have a 150 Mbps committed information rate. For the design of this new service, which QoS mechanism must be used to ensure low packet loss within the service provider network?
A. policing
B. LLQ
C. shaping
D. CBWFQ
Answer: C
NEW QUESTION 722
Which statement about traffic shaping is true?
A. It works by minimizing data transmission intervals.
B. It separates data packets based on certain characteristics by using NBAR.
C. It regulates data transmission patterns into the network.
D. It enforces an upper limit on bursty data traffic.
Answer: D
NEW QUESTION 723
A large enterprise network runs IS-IS. There is a concern that the IS-IS default metrics are not flexible enough. Which IS-IS feature enables increased granularity for traffic on the network?
A. IS-IS Wide Metrics
B. IS-IS DIS
C. IS-IS Multitopology
D. IS-IS route leaking
Answer: A
NEW QUESTION 724
Which two devices are open-source SDN controllers? (Choose two.)
A. Big Cloud Fabric
B. OpenDaylight
C. Virtual Application Networks SDN Controller
D. Application Policy Infrastructure Controller
E. OpenContrail
Answer: BE
NEW QUESTION 725
When designing a network that uses IPsec, which technique is suggested to avoid network fragmentation?
A. Reduce the MTU on the side closest to the server.
B. Reduce the MTU on both ends of the TCP connection.
C. Reduce the MTU on the side closest to the client.
D. Reduce the MTU only in the WAN.
Answer: B
NEW QUESTION 726
Which solution provides an active/active alternative to spanning-tree?
A. RSTP
B. TRILL
C. MST
D. Ethernet Ring Protection Switching
Answer: B
NEW QUESTION 727
When is it required to leak routes into an IS-IS Level 1 area?
A. when unequal cost load balancing is required between the backbone and non-backbone areas
B. when a multicast RP is configured in the non-backbone area
C. when equal cost load balancing is required between the backbone and non-backbone areas
D. when MPLS L3VPN PE devices are configured in the Level 1 areas
Answer: D
NEW QUESTION 728
A financial trading organization plans to monitor the network latency for multicast market data feeds on a hop-by-hop basis. Which technology must be added to their design to support requirement?
A. NBAR
B. IPFIX
C. PTP
D. SPAN
Answer: B
NEW QUESTION 729
When designing fast convergence on a network using a loop-free alternate, on which two bases can the next-hop routes be precomputed? (Choose two.)
A. per neighbor
B. per failure type
C. per prefix
D. per link
E. per network type
Answer: CD
NEW QUESTION 730
Which markup language is used to format Ansible’s playbook?
A. ADML
B. YAML
C. XML
D. HTML
E. NAML
Answer: B
NEW QUESTION 731
Drag and Drop
Drag and drop the optical technology design characteristics on the left to the correct optical technologies on the right. Not all options are used.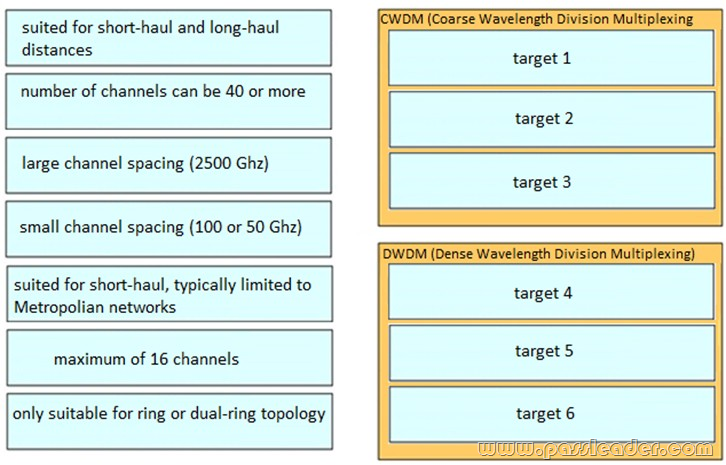
Answer: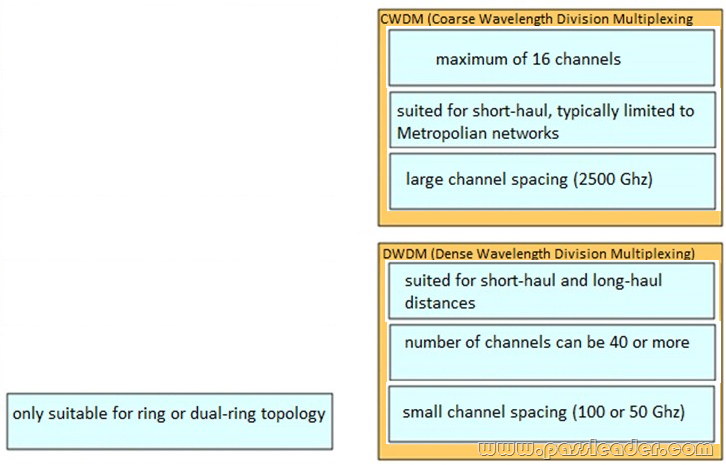
NEW QUESTION 732
Which ISAKMP feature can be used to reduce device CPU load by not sending keepalive messages for known active ISAKMP security associations?
A. DPD
B. IKEv2
C. SPI
D. Main Mode
Answer: A
NEW QUESTION 733
A large enterprise network has two data centers and a WAN edge in a hub-and-spoke network topology. The entire network is in a single OSPF area. Spoke routers are connected to unreliable WAN links. Which two changes must be made to deploy LSA filtering on the spoke routers? (Choose two.)
A. Configure the hub routers as ASBRs.
B. Keep the spoke routers in normal areas.
C. Configure the hub routers as ABRs.
D. Place spoke routers in totally stubby areas.
E. Place spoke routers in stub areas.
Answer: CD
NEW QUESTION 734
The BGP table contains hundreds of thousands of routes. Which design technique improves the convergence time?
A. Enable TCP path MTU discovery to every neighbor.
B. Use TCP ports higher than 1024 for your BGP sessions.
C. Deploy BGP route reflectors instead of full-mesh iBGP.
D. Deploy BGP confederations within your backbone.
Answer: C
NEW QUESTION 735
You must make IGP redesign recommendation for a client that has old equipment, with low CPU power and memory, that they do not have budget to replace. They are very concerned about CPU load on the routers. They are using IS-IS as the IGP in a single Layer 1 area and all routers are connected to each other with point-to-point links. Which method do you recommend to reduce or limit CPU overhead caused by IS-IS?
A. Implement wide style metrics for IS-IS on all routers.
B. Use mesh groups to limit flooding of LSAs.
C. Select a router to act as a pseudonode to limit topology synchronization.
D. Divide the routers into multiple areas and implement address summarization.
Answer: D
NEW QUESTION 736
……
Download the newest PassLeader 352-001 dumps from passleader.com now! 100% Pass Guarantee!
352-001 PDF dumps & 352-001 VCE dumps: https://www.passleader.com/352-001.html (738 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. New CCDE 352-001 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpflFYOFdyS1ctQVc2X1cwT0d2R2dyZzBsb2hPaGw5V2Y5akx5QmxxYUdOOUU