100% Pass 70-680 Exam: if you are preparing 70-680 exam and want to pass it exam easily, we recommend you to get the new 580q 70-680 exam questions from PassLeader, we PassLeader now are sharing the latest and updated 70-680 braindumps with VCE and PDF file, we have corrected all the new questions of our 70-680 VCE dumps and 70-680 PDF dumps and will help you 100% passing 70-680 exam.
keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 practice test,70-680 vce dumps,70-680 study guide,70-680 braindumps,TS: Windows 7, Configuring Exam
QUESTION 461
All client computers in your company network have Windows 7 Professional installed. The computers are configured with automatic scheduled Microsoft updates installation. You receive a support call indicating that after the recently installed update, one of the business applications is unable to start on the computers. You need to remove the most recent Microsoft update from the computers. What should you do first?
A. From the Programs and Features, open the Installed Updates window.
B. From the Services console, open the Windows Update service.
C. From the Event Viewer, open the System log.
D. From the Task Scheduler, view the WindowsBackup node.
QUESTION 462
Hotspot Question
A company has Windows 7 computers that that use Internet Explorer 10 with InPrivate Browsing and InPrivate Filtering. In the table below, identify the functionality of each InPrivate mode. (Make only one selection in each column. This question is worth two points. )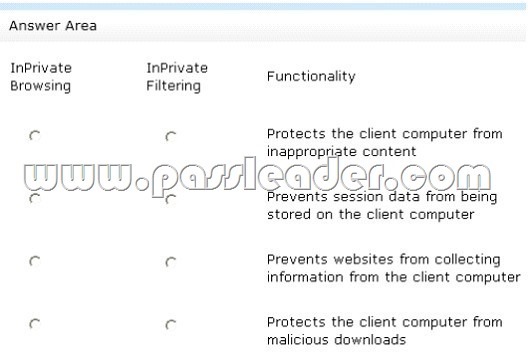
Answer: 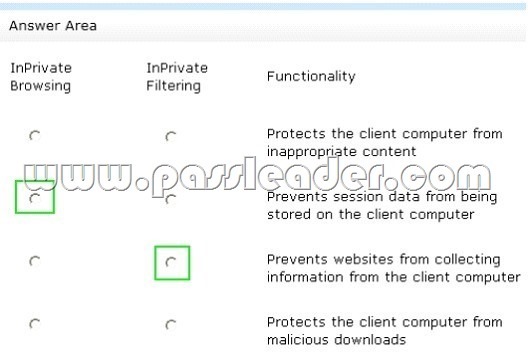
QUESTION 463
You are a desktop administrator for an enterprise organization. A user applies a device update from the manufacturer, and now the computer is displaying error messages. The user has critical documents on the computer that need to be preserved. You need to restore the computer to an operating state and preserve applications and data. What should you do?
A. Perform a re-installation of Windows.
B. Perform a System Image Recovery.
C. Boot Windows by using the Last Known Good Configuration.
D. Restore Windows by using the most recent System Restore point.
Answer: D
QUESTION 464
You have a computer that runs WindowsXP. The computer has one partition. You install Windows 7 on the computer. You need to migrate a user profile from the Windows XP installation to Windows 7 installation. What should you do first?
A. From Windows 7, run Scanstate.exe /offlineWinOld:c:\windows.
B. From Windows 7, run Scanstate.exe /offlineWinOld:c:\windows.old.
C. At the command prompt, run Xcopy /s /e c:\windows\users\*.* c:\users\.
D. At the command prompt, run Xcopy /s /e c:\windows.old\documents and settings\*.*c:\users\.
Answer: B
Explanation:
/offlinewinold: “Windows.old diredctory”
This command-line option enables the offline migration mode and starts the migration from the location specified. It is only intended to be used in Windows.old migration scenarios, where the migration is occurring from a Windows.old directory.
NOT Xcopy. Copies files and directories, including subdirectories. /s Copies directories and subdirectories, unless they are empty. If you omit /s, xcopy works within a single directory.
QUESTION 465
You plan to deploy Windows 7 images. You need to ensure that you can deploy images using the WindowsPreinstallation Environment (Windows PE). What would you add to the Window PE Image?
A. ImageX
B. Usmtutils.exe
C. Mighost.exe
D. Loadstate.exe
Answer: A
QUESTION 466
Your company network includes client computers that have Windows 7 installed. All client computers have NetBIOS disabled. You need to view the status of all TCP/UDP ports. Which command should you run?
A. nbtstat -n
B. ipconfig /all
C. netstat -an
D. ipconfig /displaydns
Answer: C
QUESTION 467
Drag and Drop Question
Your organization has a Windows Server 2008 R2 server and Windows 7 Professional computers. Two groups require access to new applications. Each group uses a different application. You are adding 100 new computers to each group. You need to configure Windows Firewall to allow each group to access its application. Which four steps should you perform in sequence? (To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order. )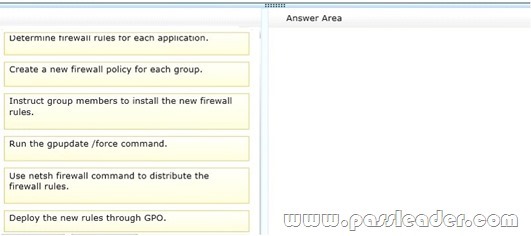
Answer: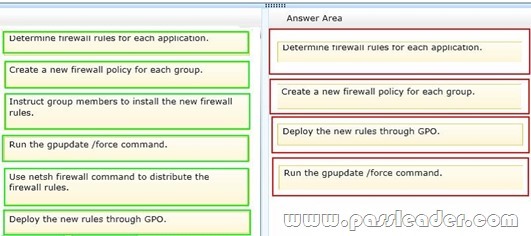
QUESTION 468
You administer computers that have Windows 7 and Internet Explorer 8 installed. You want to log on to one of the computers and access a web-based management application that runs on a server by using Internet Explorer. You need to ensure that any data about your browser session is not saved on the computer. What should you do?
A. Disable Internet Connection Sharing.
B. From the Local Group Policy, enable the InPrivate Filtering Threshold setting.
C. From the Safety drop-down menu, open an InPrivate Browsing session.
D. From Internet Options, on the Advanced tab, clear Enable DOM Storage.
Answer: C
QUESTION 469
You work as a desktop support technician at Abc.com. The Abc.com network consists of a single Active Directory domain named Abc.com. You are responsible for maintaining Abc.com’s Windows 7 workstations. You want to configure all Windows 7 workstations to produce a new Security ID (SID) as well as a Welcome screen when the workstation is booted. What should you do?
A. You should consider running Msconfig.exe /oobe /generalize startup on all Windows 7 workstations.
B. You should consider running Sysprep.exe /audit /generalize on all Windows 7 workstations.
C. You should consider running bootcfg.exe on all Windows 7 workstations.
D. You should consider running Sysprep.exe /oobe /generalize on all Windows 7 workstations.
Answer: D
QUESTION 470
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You use a computer that runs Windows 7. Now your company assigns a task to you. You are asked to prevent users from copying unencrypted files to removable drives. What action should you perform?
A. The Trusted Platform Module (TPM) settings should be modified from a local Group Policy.
B. TPM should be initialized from the Trusted Platform Module (TPM) snap-in.
C. The BitLocker Drive Encryption settings should be modified from Control Panel.
D. The BitLocker Drive Encryption settings should be modified from a local Group Policy.
Answer: D
http://www.passleader.com/70-680.html
QUESTION 471
Drag and Drop Question
You are a systems administrator for a company that uses Windows 7 computers. The company plans on upgrading all the computers. You have configured one computer, named SOURCE, with a power plan that meets a criteria for reduced power consumption. You want to test this power plan on another computer named DEST. You need to transfer the power plan from SOURCE to DEST. Which three actions should you perform in sequence? (To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order. )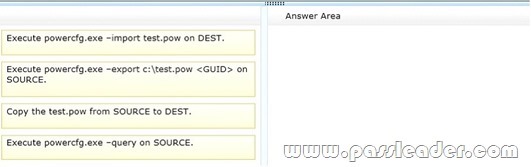
Answer: 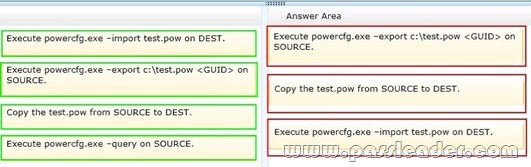
QUESTION 472
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You have a workgroup which contains five computers. Windows 7 is run by the computers. A computer named C01 has video and audio files. You have to share C01s video and audio files on the network. What should you do? (Choose more than one)
A. Connect a removable drive and enable BitLocker To Go.
B. A HomeGroup should be created.
C. The files should be moved to a Media Library.
D. All BranchCache rules should be enabled in Windows Firewall.
Answer: BC
QUESTION 473
You have 20 client computers. The computers run Windows XP. They are joined in a domain. You plan to perform a clean installation of Windows 7 on the computers. You need to transfer all users documents and settings. You must exclude music and video files. You must achieve this goal by using the minimum amount of administrative effort. What should you do first?
A. Create a config.xml file.
Configure a logon script for the Windows XP computers to launch Loadstate.exe
B. Modify the migapp.xml file.
Configure a logon script for the Windows XP computers to launch Scanstate.exe
C. Modify the miguser.xml file.
Configure a logon script for the Windows XP computers to launch Migwiz.exe
D. Modify the migdocs.xml file.
Configure a logon script for the Windows XP computers to launch Scanstate.exe
Answer: D
Explanation:
MigDocs.xml. This file contains information on the location of user documents.
NOT Config.xml. This file is different from the other migration files as it is used to exclude features from the migration. You can create and modify the Config.xml file using ScanState.exe with the /genconfig option.
NOT MigUser.xml. This file contains rules about user profiles and user data. The default settings for this file migrate all data in My Documents, My Video, My Music, My Pictures, desktop files, Start Menu, Quick Launch settings, favorites, Shared Documents, Shared Video, Shared Music, Shared desktop files, Shared Pictures, Shared Start menu, and Shared Favorites. This file also contains rules that ensure that all the following file types are migrated from fixed volumes: .qdf, .qsd, .qel, .qph, .doc, .dot, .rtf, .mcw, .wps, .scd, .wri, .wpd, .xl*, .csv, .iqy, . dqy, .oqy, .rqy, .wk*, .wq1, .slk, .dif, .ppt*, .pps*, .pot*, .sh3, .ch3, .pre, .ppa, .txt, .pst, .one*, .mpp, .vsd, .vl*, .or6, accdb, .mdb, .pub, .xla, .xlb and .xls. The asterisk ( *) represents zero or more characters.
NOT MigApp.xml. This file contains rules about migrating application settings. These include Accessibility settings, dial-up connections, favorites, folder options, fonts, group membership, Open Database Connectivity (ODBC) settings, Microsoft Office Outlook Express mailbox files, mouse and keyboard settings, phone and modem options, Remote Access Service (RAS) connection phone book files, regional options, remote access, screen-saver settings, taskbar settings, and wallpaper settings.
QUESTION 474
You administer computers that have Windows 7 and Internet Explorer 8 installed. You want to log on to one of the computers and access a web-based management application that runs on a server by using Internet Explorer. You need to ensure that any data about your browser session is not saved on the computer. What should you do?
A. Start the Microsoft Network Access Protection service.
B. From the Safety drop-down menu, open an InPrivate Browsing session.
C. From Internet Options, on the Advanced tab, clear Enable DOM Storage.
D. From Internet Options, modify the security settings for the Internet zone.
Answer: B
QUESTION 475
You install the Windows Automated Installation Kit (WAIK) for Windows 7 on a computer that runs Windows 7. You want to deploy a Windows image (WIM) file to other computers in the domain. You need to capture the operating system, computer configuration, and applications installed on the computer to a WIM file. What should you do before you capture the image?
A. Start the computer by using the Windows Preinstallation Environment (WinPE) ram disk.
B. Run ScanState.exe.
C. Run Defrag.exe.
D. Run Diskpart.exe.
Answer: B
Explanation:
You use ScanState to save user state data. By default, this program places user state data into the data store location as defined by the three migration.xml files.
QUESTION 476
You are a network administrator for Southbridge Video, a company that records and processes videos. Your network consists of Windows 7 computers and Windows Server 2008 R2 servers. Management secures a contract to provide closed captioning a large number of videos. They open a new, remote location with a slow network link and hire temporary staff to perform the work. The videos that the users need to view are on a file share on the corporate network. Users may have to view the video files multiple times to complete their work. You need to ensure that the slow network link is used as efficiently as possible. What should you do?
A. Enable transparent caching.
B. Enable folder redirection.
C. Use DirectAccess to connect to the share.
D. Configure the client machines to use offline file synchronization.
Answer: A
QUESTION 477
You use a computer that has Windows 7 SP1 installed and has a folder named C:\Data. The active network connection of the computer is configured as Public. You use Advanced Sharing to share a folder as shown in the exhibit. (Click the Exhibit button.)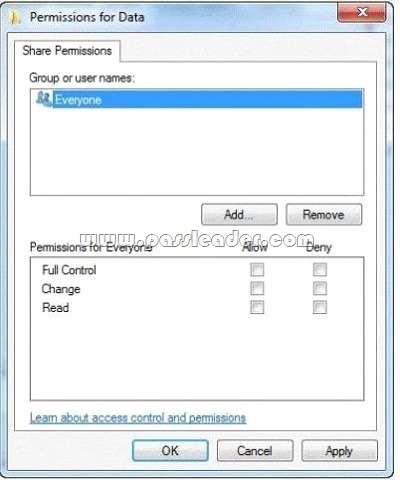
A user attempts to access the shared folder across the network and receives the following error message:
“Access is Denied.”
You need to ensure that the user can download files from the shared folder. What should you do?
A. Allow file and printer sharing through Windows Firewall. From the Security settings of the folder, assign the Full Control NTFS permission to the user.
B. From the Advanced Sharing settings of the folder, assign the Read share permission to the user.
C. From the Security settings of the folder, assign the Read NTFS permission to the user.
D. Change the network location of the computer from a Public network to a Home or Work network.
Answer: C
Explanation:
Assuming the user has appropriate Share permissions, he would still need NTFS permissions.
QUESTION 478
You have a computer that runs Windows 7. The computer is a member of a workgroup. You use Encrypting File System (EFS) to protect your local files. You need to ensure that you can decrypt EFS files on the computer if you forget your password. What should you do?
A. From Authorization Manager, modify the Authorization Manager options.
B. From Credential Manager, select Back up vault.
C. Create an EFS Data Recovery Agent by using Group Policy.
D. From User Accounts, select Manage your file encryption certificates.
Answer: C
Explanation:
Data Recovery Agent (DRA) is a user account that has been granted permissions to access all encrypted files even if the files have been encrypted using encryption key of another user account of the computer. Administrators must create and configure Data Recovery Agents before allowing users to encrypt their files. This serves as a proactive step taken by the administrators as once user account that has encrypted the file has been deleted from the computer, in the absence of DRA the files cannot be recovered whatsoever.
QUESTION 479
You work in an international company which is named Wiikigo. Before entering this company, you have two years of experience in the IT field, as well as experience implementing and administering any Windows client operating system in a networked environment. You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and configuring Hardware and Applications and son on. You manage a computer that runs Windows 7. You have to identify which applications were installed during the last week. So what action should you perform?
A. The System Performance Data Collector Set should be run from Performance Monitor.
B. The informational events should be reviewed from Reliability Monitor.
C. The Software Environment should be reviewed from System Information.
D. The System Diagnostics Report should be reviewed from Performance Monitor.
Answer: B
QUESTION 480
You manage a network device by using a web interface. You perform all critical Windows updates so that the computer now runs Internet Explorer 10. After performing these updates, the layout of the network device web page displays incorrectly. Other web pages display correctly. You need to resolve this issue. What should you do?
A. Clear Internet Explorer’s browsing history.
B. Enable Compatibly Mode for the network device web page.
C. Set the local Intranet security zone to Low.
D. Add the network device web page to the trusted sites zone.
Answer: D