100% Valid 70-680 Exam Pass Tips: PassLeader’s 580q 70-680 exam dumps were updated in recent days with new 70-680 exam questions added, PassLeader ensure the latest 70-680 VCE dumps or PDF dumps are the newest and the most valid, our 70-680 practice tests will help you 100 percent pass 70-680 exam. Visit passleader.com and get the 70-680 exam questions with PDF and VCE. New version VCE player is also free now.
keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 vce dumps,70-680 braindumps,70-680 practice tests,70-680 study guide,TS: Windows 7, Configuring Exam
QUESTION 171
You are the network manager for a small company. You have a junior IT administrator who did some installations last week on a Windows 7 machine. How can you see what applications were installed last week on the Windows 7 machine?
A. View the informational events of Reliability Monitor.
B. Open Control Panel, Add/Remove programs.
C. Check Event Viewer system logs.
D. View the data collector sets.
Explanation:
By viewing the informational events of Reliability Monitor, you will be able to see which application got installed by the installation date.
QUESTION 172
You are the network administrator for Stellacon Corporation. Users in the sales department have been complaining that the Sales application is slow to load. Using Performance Monitor, you create a baseline report for one of the computers, monitoring memory, the processor, the disk subsystem, and the network subsystem. You notice that the disk subsystem has a high load of activity. What other subsystem should you monitor before you can know for sure whether you have a disk subsystem bottleneck?
A. Memory
B. Processor
C. Network
D. Application
Answer: A
Explanation:
You should check the memory counters. If your computer does not have enough memory, it can cause excessive paging, which may be perceived as a disk subsystem bottleneck.
QUESTION 173
Your accounting department runs a processor – intensive application and you are trying to determine whether their current computers need to have the processors upgraded. You load a test computer with a configuration identical to the production computers’ and run a program that simulates a typical user’s workload. You monitor the Processor > % Processor Time counter. What average value for this counter would indicate a processor bottleneck?
A. Over 5 percent
B. Over 50 percent
C. Over 60 percent
D. Over 85 percent
Answer: D
Explanation:
If the average Processor > % Processor Time counter is consistently above 85 percent, a processor bottleneck may be indicated. Normally this number will spike up and down over time. A spike over 85 percent is not necessarily alarming. If the average is over 85 percent, then a bottleneck is indicated and a second processor or a faster one should be installed.
QUESTION 174
You are the network administrator for a large corporation. The accounting department requires that a specific application, STELLAPP.EXE , be run every day to create daily reports on accounting activity. The application needs to be run at 6 p.m. on Monday through Friday. The accounting manager has asked you to automate the process so reports are generated on the specified schedule without any user interaction. Which Windows 7 utility should you use?
A. Task Scheduler
B. Automated Scheduler
C. Task Manager
D. Task Automater
Answer: A
Explanation:
To automate scheduled tasks, you use Task Scheduler. You can schedule tasks to be run based on the schedule you specify and the user account that should be used to run the task.
QUESTION 175
You are the network administrator for a large company. The payroll manager has Windows 7 installed on her desktop computer. The computer has the following configuration:
Dual Pentium 4 processors
1 GB of RAM
Two physical SCSI disks
Disk 0 has volume C:
Disk 1 has volume D:
1.5 GB page file on partition C:
100 Mbps Fast Ethernet NIC
The payroll manager requires the use of a database application. She has come to you to report that when the database application is running, the computer slows down very signifi cantly, and she is unable to run any other applications. You run Reliability and Performance Monitor on her computer and record the following information when the database application is running:
– Sustained processor utilization is at 100 percent for both processors.
– There are a significant number of hard page faults.
When you record the data for the computer when the database application is not running, you record the following information:
– Average processor utilization is at 30 percent.
– There are a significant number of hard page faults.
The database application is critical to the fi nance manager’s job. In order to be able to better manage her productivity, which two of the following actions will have the greatest impact on optimizing her computer’s performance? Choose two.
A. Upgrade the processors in her computer.
B. Add memory to the computer.
C. Split the page file over D: and E:.
D. Increase the page file to 3 GB.
Answer: AB
Explanation:
The greatest improvement in performance for this computer can be obtained by upgrading the processors and adding more physical RAM. Because the database application is using 100 percent processor utilization over a sustained period, you need to upgrade the processors. The hard page faults indicate that you also have a memory bottleneck. Although moving or increasing the page file might have an impact on performance, neither would have as large an impact as adding more physical memory.
QUESTION 176
You are the network administrator for an organization that has decided to migrate to Windows 7. Part of your job requires that you are able to complete the following:
– Collect data from the local or remote Windows 7 computers on the network. You can collect data from a single computer or multiple computers concurrently.
– View data as it is being collected in real time, or historically from collected data.
Which Windows 7 application can you use to achieve your task?
A. Event Viewer
B. Computer Monitor
C. Windows 7 Monitor
D. Performance Monitor
Answer: D
Explanation:
Performance Monitor enables you to collect data from your local computer or remote Windows 7 machine, from a single computer or multiple computers concurrently; view data as it is being collected in real time, or historically from collected data; have full control over the selection of what data will be collected, by selecting which specifi c objects and counters will be collected; choose the sampling parameters that will be used, meaning the time interval that you want to use for collecting data points and the time period that will be used for data collection.
QUESTION 177
You are the network administrator for a large organization. You are running Windows 7 machines throughout your network along with Windows Server 2008 R2. You need to use Event Viewer to review event logs for Critical and Error events only. You need to see all of these events from the logs. What do you do to achieve this?
A. Use the Administrative Events view.
B. Create a custom view and choose Administrative Events.
C. Do a search on the system log for all of these events.
D. Create a custom view and select Critical, Error, and Verbose for all logs.
Answer: D
Explanation:
You would have to create a custom view to achieve this task. You could not use the Administrative Events view (default custom view) because it also includes all warnings.
QUESTION 178
You are the network administrator for an organization that runs Windows Server 2008 R2 and Windows 7. You are asked by your IT manager to collect performance data on a Windows 7 machine, for a period of three weeks. The IT manager wants CPU utilization, disk utilization, and memory utilization all included in the data collected. How should you accomplish this?
A. Create a user – defined data collector set.
B. Create a custom performance set.
C. Create a trace event.
D. Create a session data collector set.
Answer: A
Explanation:
Data collector sets are used to collect data into a log so the data can be reviewed.You can view the log files with Performance Monitor.
QUESTION 179
While using Performance Monitor, you use the following output mode. Which output mode are you using?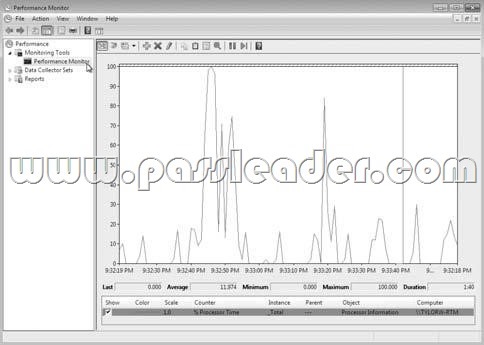
A. Histogram bar view
B. Graph view
C. Report view
D. Line view
Answer: D
Explanation:
The graphic is an example of a line view output. The three options are line view, histogram bar view, and report view.
QUESTION 180
While using Performance Monitor, you use the following output mode.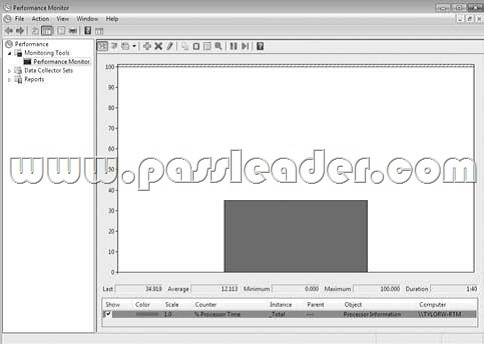
Which output mode are you using?
A. Histogram bar view
B. Graph view
C. Report view
D. Line view
Answer: A
Explanation:
The graphic is an example of a histogram bar view output. The three options are line view, histogram bar view, and report view.
http://www.passleader.com/70-680.html
QUESTION 181
A company has client computers that run Windows Vista. You need to install Windows 7 on a client computer in a dual-boot configuration with the existing Windows Vista installation, without reducing the size of the partition that contains Windows Vista. Which actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)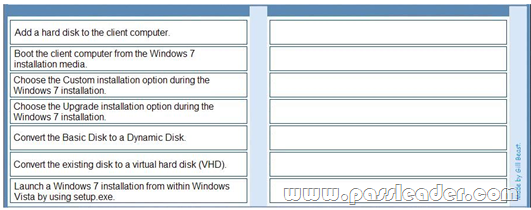
Answer: 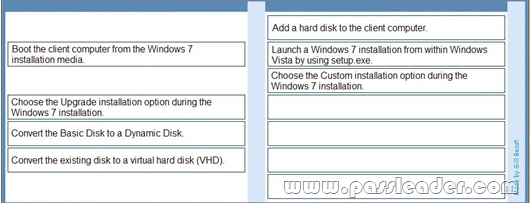
QUESTION 182
You have 15 computers that run Windows 7. You need to implement a monitoring solution that meets the following requirements:
– Sends an e-mail notification when an application error is logged in the event log.
– Runs a script to restart the computer if an application error occurs between 17:00 and 07:00.
– Minimizes the administrative effort required to monitor applications.
What should you do?
A. On all the computers, configure a custom view. Configure a custom task for the application error events.
B. On a computer, configure a custom view to display the application errors. Configure a custom task for the application error events.
C. On a central computer, configure an event subscription. On all of the computers, configure a custom task in the Forwarded Events log.
D. On all the computers, configure an event forwarding to a central computer. On the central computer, configure a custom task in the Forwarded Events log.
Answer: D
Explanation:
Event ForwardingEvent forwarding enables you to transfer events that match specific criteria to an administrative (or collector) computer. This enables you to manage events centrally. A single event log on the collector computer holds important events from computers anywhere in your organization. You do not need to connect to the local event logs on individual computers. SubscriptionsIn a source-initiated subscription (sometimes termed a source computer-initiated subscription), the computer on which an event is generated (the source computer) sends the event to the collector computer. You would use a source-initiated subscription when you have a large number of source computers and you configure these computers through Group Policy.
QUESTION 183
You have a computer that runs Windows 7. You have a system image of the computer. You need to restore a single file from the system image. You must achieve the goal using minimum administrative effort. What should you do?
A. From Disk Management, select Attach VHD.
B. From the Backup and Restore, select Restore my files.
C. Restart the computer and run system restore.
D. Restart the computer and run system image recovery.
Answer: A
Explanation:
Attach VHD:
Attaching a VHD activates the VHD so that it appears on the host computer as a local hard disk drive. This is sometimes called “surfacing a VHD” because the VHD is now visible to users. If the VHD already has a disk partition and file system volume when you attach it, the volume inside the VHD is assigned a drive letter. The assigned drive letter is then available for use, similar to when you insert a USB flash drive into a USB connector. All users (not just the current user) can use the attached VHD in the same way they use other volumes on local physical hard disk drives (depending on security permissions). Furthermore, because you can attach a VHD that is located on a remote server message block (SMB), you can manage your images remotely. Once attached the single file can be restored. The other answers are overkill or replace all files not just the one required.
http://technet.microsoft.com/en-us/library/dd440865%28WS.10%29.aspx
What is system protection?
System protection is a feature that regularly creates and saves information about your computer’s system files and settings. System protection also saves previous versions of files that you’ve modified. It saves these files in restore points, which are created just before significant system events, such as the installation of a program or device driver. They’re also created automatically once every seven days if no other restore points were created in the previous seven days, but you can create restore points manually at any time. System protection is automatically on for the drive that Windows is installed on. System protection can only be turned on for drives that are formatted using the NTFS file system. There are two ways that you can take advantage of system protection:
* If your computer is running slowly or isn’t working properly, you can use System Restore to return your computer’s system files and settings to an earlier point in time using a restore point.
* If you accidentally modify or delete a file or folder, you can restore it to a previous version that’s saved as part of a restore point.
QUESTION 184
You administer desktops that have 32-bit and 64-bit versions of Windows 7 Enterprise SP1 installed. All desktops have a single CD-RW drive. The local hard disk drives on all computers are partitioned with a recovery partition and a single logical drive C. You need to be able to restore Windows boot files on any of The desktops if the boot files become corrupted. Which two actions should you perform? (Each correct answer presents a part of the solution. Choose two.)
A. A. Create a system image of a Windows 7 Enterprise 64-bit desktop
B. Create a system repair disk on a Windows 7 Enterprise 64-bit desktop.
C. Restart Windows 7 Enterprise 64-bit desktops. Select the Disable Driver Signature Enforcement option from the Advanced Boot Options menu.
D. Enable system protection on the recovery partition on 64-bit desktops.
E. Create a system repair disk on a Windows 7 Enterprise 32-bit desktop.
F. Create a system image of a Windows 7 Enterprise 32-bit desktop.
G. Enable system protection on the recovery partition on 32-bit desktops.
Answer: BE
Explanation:
http://windows.microsoft.com/en-US/windows7/Create-a-system-repair-disc
QUESTION 185
You administer a computer that has Windows 7 and Internet Explorer 8 installed. You discover that two users have installed a new toolbar into their browsers. The toolbar is using an unapproved search engine. You need to prevent the users from using the unapproved search engine. What should you do?
A. From programs and features in the control panel, uninstall the toolbar.
B. From Internet Explorer, delete the browsing history and locally stored files.
C. Start Internet Explorer in an InPrivate Browsing session.
D. From an elevated command prompt, run %systemdrive%\program files\Internet explorer\iecleanup.exe.
Answer: A
QUESTION 186
You have a computer that runs Windows 7. You need to provide standard users the ability to update the drivers for display adapters. What should you modify from the Local Group Policy?
A. Driver installation settings for the user
B. Device installation settings for the computer
C. Driver installation settings for the computer
D. Display settings for the user
Answer: C
Explanation:
To Update the Drivers you need permissions to install drivers. Apply this to the computer for all local users, as opposed to only one user.
QUESTION 187
You administer a computer that has Windows 7 Enterprise installed. The computer has an application that must run by using administrative permissions. A user who has a standard user account connect to the computer by using a Remote Desktop Connection. The user right-clicks the application shortcut, but the Run as administrator option is unavailable. You need to ensure that the user is able to run the application by using administrative permissions. What service should you configure? (To answer, select the appropriate option or options in the answer area.)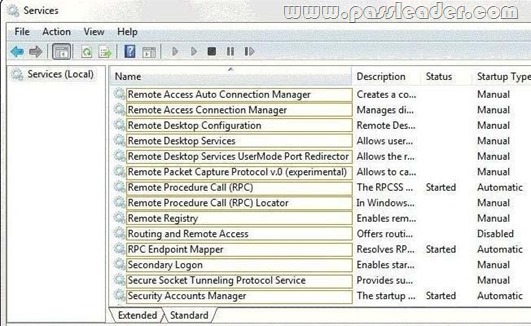
Answer: 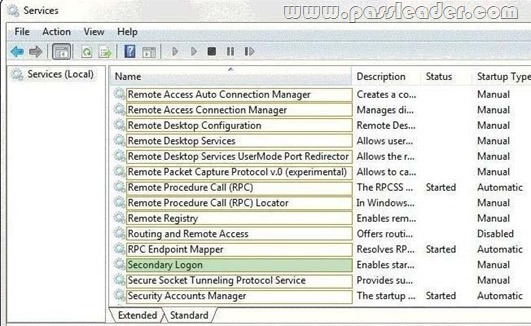
QUESTION 188
You administer client computers that have Windows 7 Professional SP1 64-bit installed. All the computers are members of a single Active Directory domain. You need to prevent users from installing non-trusted device drivers. What should you do?
A. Enable the Code signing for device drivers in a domain Group Policy.
B. Disable the Code signing for device drivers in a domain Group Policy.
C. Add each user to a Domain Admins group.
D. Run the sigverif.exe command on each computer.
Answer: A
Explanation:
Can’t see any of the rest PREVENTING users from installing non trusted devices – but Sigverig does highlight them.
QUESTION 189
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
A company has client computers that run Windows 7 Enterprise. A user is asked to remove encryption from a locally saved folder so that other users can read and write to that folder. You need to verify that the folder is not encrypted with the Encrypting File System (EFS). What should you use to accomplish this goal?
A. Device Manager
B. Local Users and Groups
C. The User Account Control Settings Control Panel window
D. The Icacls command
E. The Group Policy Management console
F. Share permissions
G. The Netsh command
H. The Services Management console
I. The Folder Properties window
Answer: I
Explanation:
http://technet.microsoft.com/en-us/windows/how-do-i-get-started-with-the-encrypting-file-system-in-windows-7.aspx
QUESTION 190
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
A company has client computers that run Windows 7 Enterprise. You need to ensure that only signed and validated executable files are run with elevated privileges. What should you use to accomplish this goal?
A. The Group Policy Management console
B. The Netsh command
C. The Service Management console
D. The Folder Properties window
E. Share permissions
F. The Icacls command
G. Device Manager
H. The User Account Control Settings Control Panel windows
I. Local Users and Groups
Answer: A
http://www.passleader.com/70-680.html
QUESTION 191
You support Windows 7 client computers used by Marketing department employees. The computers have dual-core CPUs for generating rich media advertisements. The Marketing department employees are reporting CPU performance issues while rendering the rich media advertisements. You need to configure the wmplayer.exe process to use only a single CPU core. What should you do? (To answer, select the appropriate option or options in the answer area.)
Answer: 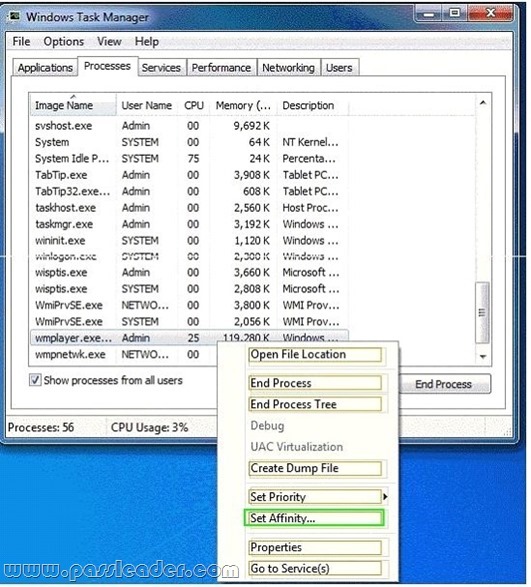
QUESTION 192
You use a computer that has Windows 7 Enterprise installed. The computer has a single 500-GB hard disk. You install two new 1-TB hard disks. You need to configure the new disks in a fault-tolerant configuration. What should you do? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer: 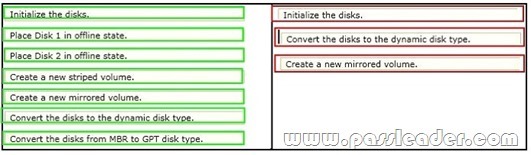
QUESTION 193
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series. Your company office network includes a file server that has Windows Server 2008 R2 installed and client computers that have Windows 7 Enterprise installed. The computers are members of an Active Directory domain. The file sender has the BranchCache feature installed. You create a shared folder on the server and enable BranchCache on the shared folder. You discover that the users of the client computers are unable to access files in the shared folder. You need to provide access for the users to the shared folder. What should you do?
A. Run the Netsh branchcache set service mode= HOSTEDSERVER clientauthentication=NONE command.
B. Configure firewall exception rules for multicast traffic, inbound and outbound traffic for local UDP port 3702, and inbound and outbound traffic for local TCP port 80.
C. Create a Group Policy that sets Hash Publication for BranchCache as disabled.
D. Run the Netsh branchcache set service mode=DISTRIBUTED command.
E. Create a Group Policy object and configure the Set percentage of disk space used for client computer cache option.
F. Check permissions.
G. Run the Netsh branchcache set service mode=HOSTEDCLIENT command.
H. Create a Group Policy object and enable the Set BranchCache Hosted Cache mode policy.
I. Configure firewall exception rules for inbound and outbound traffic for local TCP port 80 and for inbound and outbound traffic for local TCP port 8441.
Answer: F
Explanation:
Have the users been given access to the files (what does BranchCache have to do with accessing files locally etc).
QUESTION 194
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
Your company office network includes a file server that has Windows Server 2008 R2 installed and client computers that have Windows 7 Enterprise installed. The computers are members of an Active Directory domain. The file server has the BranchCache feature installed. You add new client computers the network. The computers have Windows 7 installed and are members of a workgroup. You need to ensure that the new client computers are configured to cache and share files. What should you configure on the new client computers?
A. Configure firewall exception rules for inbound and outbound traffic for local TCP port 80 and for inbound and outbcund traffic for local TCP port 8443.
B. Check permissions.
C. Create a Group Policy that sets Hash Publication for BranchCache as disabled.
D. Run the Netsh branchcache set service mode=HOSTEDCLIENT command.
E. Create a Group Policy object and enable the Set BranchCache Hosted Cache mode policy.
F. Create a Group Policy object and configure the Set percentage of disk space used for client computer cache option.
G. Run the Netsh branchcache set service mode=HOSTEDSERVER clientauthentication=NONE command.
H. Run the Netsh branchcache set service mode=DISTRIBUTED command.
I. Configure firewall exception rules for multicast traffic, inbound and outbound traffic for local UDP port 3702, and inbound and outbound traffic for local TCP port 80.
Answer: H
QUESTION 195
Note: This QUESTION is part of a series of QUESTIONs that use the same set of answer choices. Ananswer choice may be correct for more than one QUESTION in the series.
Your company office network includes a file server that has Windows Server 2008 R2 installed and client computers that have Windows 7 Enterprise installed. The computers are members of an Active Directory domain. The File server has the BranchCache feature installed. All client computers have Windows Firewall along with Advanced Security enabled for all network profiles. You need to ensure that client computers, can access cached files stored on the file server. What should you do?
A. Run the Netsh branchcache set service mode=HOSTEDSERVER clientauthentication=NONE command.
B. Create a Group Policy that sets Hash Publication for BranchCache as disabled.
C. Run the Netsh branchcache set service mode=DISTRIBUTED command.
D. Check permissions.
E. Configure firewall exception rules for multicast traffic, inbound and outbound traffic for local UDP port 3702, and inbound and outbound traffic for local TCP port 80.
F. Run the Netsh branchcache set service mode=HOSTEDCLIENT command.
G. Configure firewall exception rules for inbound and outbound traffic for local TCP port 80 and for inbound and outbound traffic for local TCP port 8443.
H. Create a Group Policy object and enable the Set BranchCache Hosted Cache mode policy.
I. Create a Group Policy object and configure the Set percentage of disk space used for client computer cache option.
Answer: F
QUESTION 196
You administer client computers that have Windows 7 Enterprise installed. A server named Server1 has an IP address of 10.10.4.56. The server accepts Remote Desktop connections at a custom port 10876. You need to connect to the server from a client computer by using Remote Desktop. What should you do?
A. From an elevated command prompt, run mstsc.exe /v:Server1:10876.
B. From an elevated command prompt, run mstsc.exe 10.10.4.56 port: 10876.
C. From an elevated command prompt, run mstsc.exe Server1 port:10876.
D. From the Advanced tab of your Remote Desktop connection, configure the IP address and port of Server1 as the RD Gateway Server.
Answer: A
QUESTION 197
Your company network includes client computers that have Windows 7 installed. The computers are members of an Active Directory domain and receive Windows Firewall configuration through Group Policy, A user indicates that he is unable to connect to a remote FTP server. You need to view the status of TCP/UDP ports at the user’s computer. Which command should you run?
A. Netstat -o
B. Nbtstat -a
C. Ipconfig /all
D. Netstat -an
Answer: D
QUESTION 198
Your company network has a single-domain Active Directory forest. The forest functional level is set to Windows Server 2008 R2. All computers are members of the domain. You plan to deploy Windows BitLocker Drive Encryption (BitLocker) on portable computers that have Windows 7 Enterprise installed. You need to be able to automatically back up recovery passwords for BitLocker-protected disk volumes on the portable computers. What should you do before you start encrypting the disk volumes with BitLocker?
A. Run the cscript Add-TPMSelfWriteACE.vbs script on the portable computers.
B. Run the cscript List-ACEs.vbs script on the portable computers.
C. Run the cscript Get-TPMOwnerInfo.vbs script on the client computers.
D. Select the Turn on Bitlocker backup to Active Directory option in local policy on the portable computers.
Answer: D
QUESTION 199
You use a client computer named Accounting that has Windows 7 SP1 installed. The computer allows connections from other computers that have any version of Remote Desktop installed. The computer has a locally attached printer shared as Printer1. An Accounting Users group is a member of the local Remote Desktop Users group on the computer. Only the Accounting Users group has access to Printer1. A user named User1 is a member of Accounting Users. You need to configure the computer to meet the following requirements:
– Prevent User1 from establishing Remote Desktop sessions to the Accounting computer.
– Allow other members of Accounting Users to connect to the Accounting computer by using Remote Desktop.
– Ensure that User1 can access Printer1.
What should you do?
A. Remove the Accounting Users group from the Remote Desktop Users group.
B. Remove User’ from the Accounting Users group.
C. Assign the Deny access to this computer from the network user right to User1.
D. Assign the Deny log on through Remote Desktop Services user right to User1.
Answer: D
Explanation:
D is the only method that can achieve this without affecting other groups. A and B could be equally valid by adding an additional step (adding individual users to resources).
QUESTION 200
You administer desktops computers that have Windows XP Professional SP3 64-bit installed. The computers have the Volume Shadow Copy Service (VSS) enabled on all drives. You want to migrate user profiles to Windows 7 using the User State Migration Tool (USMT) 4.0. You also plan to migrate files from the user profiles even if the files are locked by applications. You need to capture user profiles and locked files. What should you do on the Windows XP computers?
A. Stop the VSS before running scanstate.exe.
B. Stop the VSS before running loadstate.exe.
C. Run scanstate /vsc.
D. Run scanstate /hardlink.
Answer: C
Explanation:
http://technet.microsoft.com/en-us/magazine/dd443646.aspx