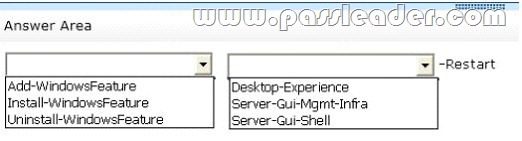
This question is provided by braindump2go.com 70-410,70-410 exam,70-410 exam dumps,70-410 exam quextions.
Question 6
You work as an administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers on the ABC.com network have Windows Server 2008 R2 installed. Some of ABC.com’s workstations have Windows 7 installed, while the rest have Windows 8 installed.
After installing a new Windows Server 2012 computer in the ABC.com domain, you configure it to run the File and Storage Services server role. You are instructed to create a shared folder on the new server, and configure the use of Previous Versions for restoring files located in the shared folder.
Which of the following actions should you take?
A. You should consider configuring the Shadow Copies settings on the new server.
B. You should consider configuring the Snapshot settings on the new server.
C. You should consider configuring the Background Copy settings on the new server.
D. You should consider configuring the Permission settings on the new server.
Answer: A
Explanation:
What are previous versions?
Previous versions are either backup copies (copies of files and folders that you back up by using the Back Up Files wizard, or shadow copies) copies of files and folders that Windows automatically saves as part of a restore point. (Shadow copies can be copies of files on your computer or shared files on a computer on a network.) You can use previous versions of files to restore files that you accidentally modified or deleted, or that were damaged. Depending on the type of file or folder, you can open, save to a different location, or restore a previous version.
ATT: ( nothing to do with question but cool to know )
File Server Volume Copy Shadow Service (VSS) Agent Service
Enables consistency of application snaphots (shadow copies). With previous versions of Windows Server, VSS only supported shadow copies of data on the local server. With WS2012, Microsoft has added VSS for SMB File Shares which extends shadow copy support for network volumes.Administrators install the FS VSS Agent on the file server where the application data is located. They then install the VSS provider in the server where the application is located. The provider talks to the agent using the new File Server Remote VSS protocol in order to manage the shadow copies of the data.
http://windows.microsoft.com/en-gb/windows-vista/previous-versions-of-files-frequently-asked-questions
Question 7
Your network contains an Active Directory domain named contoso.com.
Your company hires 500 temporary employees for the summer.
The human resources department gives you a Microsoft Excel document that contains a list of the temporary employees.
You need to automate the creation of user accounts for the 500 temporary employees.
Which tool should you use?
A. The Add-Member cmdlet
B. ADSI Edit
C. The csvde.exe command
D. Active Directory Users and Computers
Answer: C
Explanation:
csvde.exe is the best option to add multiple users. as you just need to export the excel spreadsheet as a csv file and make sure the parameters are correct.
You can use Csvde to import and export Active Directory data that uses the comma-separated value format. Use a spreadsheet program such as Microsoft Excel to open this .csv file and view the header and value information.
http://support.microsoft.com/kb/327620/en-us
Question 8
Your network contains an Active Directory domain named contoso.com. The domain contains an application server named Server1. Server1 runs Windows Server 2012.
You have a client application named App1 that communicates to Server1 by using dynamic TCP ports.
On Server1, a technician runs the following command:
New-NetFirewallRule -DisplayName AllowDynamic -Direction Outbound -LocalPort 1024- 65535 -Protocol TCP
Users report that they can no longer connect to Server1 by using Appl. You need to ensure that App1 can connect to Server1.
What should you run on Server1?
A. Set-NetFirewallRule -DisplayName AllowDynamic -Action Allow
B. netsh advfirewall firewall set rule name=allowdynamic new action = allow
C. Set-NetFirewallRule -DisplayName AllowDynamic -Direction Inbound
D. netsh advfirewall firewall add rule name=allowdynamic action=allow
Answer: C
Explanation:
Set-NetFirewallRule – Modifies existing firewall rules.
You have to allow the connection INTO the server – inbound rules
http://technet.microsoft.com/en-us/library/jj573828%28v=wps.620%29.aspx
http://mikefrobbins.com/2013/02/28/use-powershell-to-remotely-enable-firewall-exceptions-on-windows-server-2012/
Question 9
You work as a senior administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers on the ABC.com network have Windows Server 2012 installed, and all workstations have Windows 8 installed.
You are running a training exercise for junior administrators. You are currently discussing a Windows PowerShell cmdlet that activates previously de-activated firewall rules.
Which of the following is the cmdlet being discussed?
A.Set-NetFirewallRule
B. Enable-NetFirewallRule
C.Set-NetIPsecRule
D.Enable-NetIPsecRule
Answer: B
Explanation:
Enable-NetFirewallRule – Enables a previously disabled firewall rule.
http://technet.microsoft.com/en-us/library/cc990290(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/jj574205.aspx
http://mikefrobbins.com/2013/02/28/use-powershell-to-remotely-enable-firewall-exceptions-on-windows-server-2012/
http://technet.microsoft.com/en-us/library/jj554869%28v=wps.620%29.aspx
Question 10
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012.
You create a new inbound rule by using Windows Firewall with Advanced Security.
You need to configure the rule to allow Server1 to accept unsolicited inbound packets that are received through a network address translation (NAT) device on the network.
Which setting in the rule should you configure?
A. Edge traversal
B. Authorized computers
C. Interface types
D. Remote IP address
Answer: A
Explanation:
Edge traversal – This indicates whether edge traversal is enabled (Yes) or disabled (No). When edge traversal is enabled, the application, service, or port to which the rule applies is globally addressable and accessible from outside a network address translation (NAT) or edge device.
Select one of the following options from the list:
Block edge traversal (default) – Prevent applications from receiving unsolicited traffic from the Internet through a NAT edge device.
Allow edge traversal – Allow applications to receive unsolicited traffic directly from the Internet through a NAT edge device.
Defer to user – Let the user decide whether to allow unsolicited traffic from the Internet through a NAT edge device when an application requests it.
Defer to application – Let each application determine whether to allow unsolicited traffic from the Internet through a NAT edge device.
http://technet.microsoft.com/en-us/library/cc731927.aspx
http://technet.microsoft.com/en-us/library/dd421713%28v=ws.10%29.aspx